5G and AI together can enhance companies’ cybersecurity levels.
Nearly a decade ago, the advent of 4G in mobile phone plans led to the swift rise in the popularity of smartphones. Today, the next generation of wireless connectivity, 5G, is standing at the crossroads of speed and low to zero latency, features envisioned to catapult the processing capabilities of AI.
As a result, AI will become much more reliable and accessible, opening up a plethora of possibilities for consumers, businesses, and society as a whole. Imagine self-driving cars, or doctors performing remote surgeries with the aid of robots and machines.
Yes, the combination promises significant breakthroughs, but also comes with its share of cybersecurity threats and challenges. Let’s discuss what impact AI and 5G will have on cybersecurity.
Impact of 5G could focus on cybersecurity strategy
Businesses gradually realize the limitation of 4G LTE in the wave of the Internet of Things. The constraints of the existing wireless network technology have made 5G a buzz word in most industries.
As 5G networks are gradually becoming a reality for 2019 and 2020, this lightning-fast network will shape businesses as it opens up transformative possibilities in the IoT space.
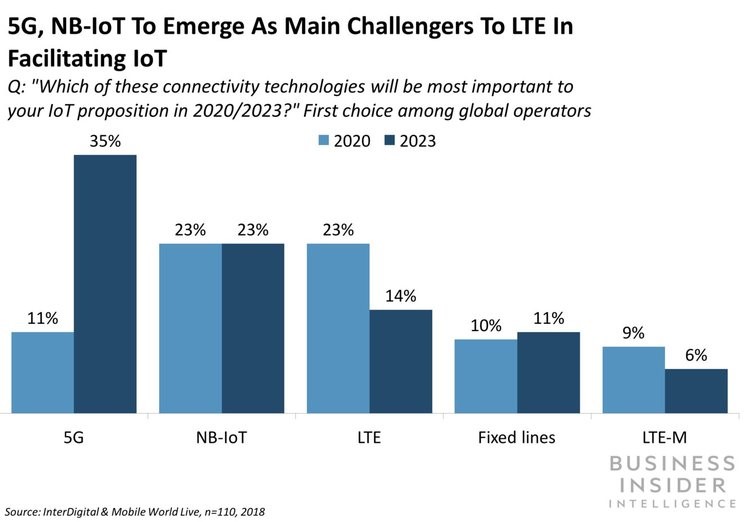
5G and 4G over facilitating IoT
As the 5G integration seems on the horizon, a team of experts in mobile and security technologies at the 2018 AT&T Business Summit discussed the future implications of 5G. The panel discussed how emerging networking technology would revolutionize the online security world. They emphasized the constraints and mistakes in the existing cybersecurity strategy and how 5G will strengthen it.
John Marinho, CTIA’s vice president of technology and cybersecurity, said that security will be more embedded and dynamic than ever before in the future. The current biggest problem in cybersecurity is poor user hygiene. Good hygiene is vital for maintaining secure network connectivity. Thus, 5G will make it critical to logging and monitoring user activity.
Undoubtedly, the introduction of 5G will enhance the cybersecurity strategy but, at the same time, it will highlight a serious challenge. More and more devices are being connected to the network, and each has a potential security risk.
With the help of smart sensors, manufacturers can monitor assembly lines in real-time. But with poorly and unsecured configurations, these devices could cause the company’s valuable and confidential data to be stolen. It will also increase the appeal of cellular solutions in the available area. In addition to this, 5G-enabled hardware will help companies support their IoT business.
AI and cybersecurity
There was a case where two hospitals — one in Ohio and another in West Virginia — failed to process emergency patient requests and sent incoming patients to nearby hospitals. Their actions were due to cyber threats being one of the top concerns, as is true for many industry leaders.
Artificial intelligence and machine learning have limitless potential in avoiding these threats to cybersecurity. Deploying AI for cybersecurity helps protect companies from existing cyber threats, such as potential malware and other threats. In addition to this, AI-powered cybersecurity systems ensure effective security standards. They help in developing and implementing highly-secure prevention and recovery strategies.
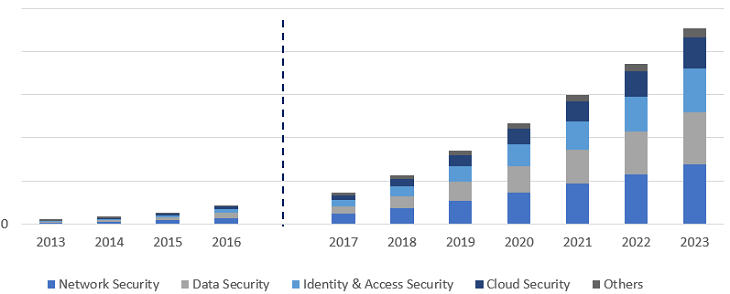
Businesses are aware of AI’s role in cybersecurity. In fact, the AI in the cybersecurity market is expected to hit more than $18Bn by 2023.
Companies often use authentication models to secure their valuable data from malicious access. If someone from the company, who has higher authentication privileges, accesses data remotely, the system can be compromised using the network on which it is accessed.
In such scenarios, conventional authentication models perform in a less agile manner. Alternatively, if companies use AI-enabled cybersecurity tools, it can help create real-time, dynamic, and a global authentication framework that grants access privileges according to the location or network.
Final words
Overall, both AI and 5G seem ready to transform the way businesses handle cybersecurity. Together, expect to strengthen cybersecurity strategies. However, at the same time, there are limitations and challenges associated with implementing these strategies securely and successfully.
For instance, Yahoo recently agreed to a $50 million settlement for a data breach, which took place in 2013. The event compromised email addresses and personal data of nearly three billion Yahoo users. Thus, companies have to work with cybersecurity experts to create effective recovery strategies proactively, as reactive strategies and processes often fail and result in pricey expenses.
There is still a great need for continuous research and development in the field of AI and 5G technologies to help companies safeguard their online businesses. With better understanding and guided implementation of these technologies, companies can safeguard their businesses from potential cyber-attacks up to a great extent.




Leave a Comment